Occupational health sits at a high-value intersection: medical data, employee identifiers, employer workflows, and time-sensitive operations such as pre-employment drug screens and fit-for-duty exams. That combination is attractive to bad actors, especially ransomware and credential theft groups, because disruption creates leverage and the data has resale value.
The good news is that the strongest defenses are not exotic. A solid baseline program, grounded in risk management, strong access controls, and meaningful audit logs, eliminates many common paths attackers use. NIST’s Cybersecurity Framework (CSF) 2.0 is a practical way to organize this work across governance, protection, detection, response, and recovery (NIST, 2024).
This paper focuses on what occupational health organizations should prioritize coming out of Cybersecurity Month and heading into 2026: secure passwords and authentication, audit logs and monitoring, ransomware resilience, vendor and integration risk, and a short “do this next” checklist.

Even when a specific data element is not regulated as HIPAA-protected health information in a given context, it is still sensitive, actionable, and damaging if exposed. That is exactly what makes it useful to criminals.
HHS has emphasized that healthcare cyberattacks are increasing in frequency and impact and has proposed updates to the HIPAA Security Rule to strengthen cybersecurity safeguards for electronic protected health information. The HHS NPRM page also highlights sharp increases in large breaches and individuals affected in recent years (HHS, 2024).
The Modern Threat Landscape: How Bad Actors Actually Get In
Healthcare and healthcare-adjacent organizations are routinely targeted by a small set of recurring tactics. Two sources are particularly helpful in framing the occupational health reality:
1.) The “Five Prevailing Threats” Lens:
The HICP (Health Industry Cybersecurity Practices) technical guidance identifies five prevailing threats: social engineering, ransomware, loss or theft of equipment or data, insider (accidental or malicious) data loss, and attacks against network-connected medical devices (HICP, 2024).
Occupational health sees all five, but social engineering plus credential theft is the starting point more often than many teams want to admit. Most ransomware campaigns begin with an identity failure somewhere.
2.) What Breaches Often Look Like in Practice
Verizon’s 2024 Data Breach Investigations Report (DBIR) shows healthcare incidents clustering around patterns like system intrusion, social engineering, and basic web application attacks, with ransomware and stolen credentials appearing frequently in those chains (Verizon, 2024).
A practical takeaway: You do not have to defend against every imaginable attack. You do have to defend against the common ones consistently.
The “Front Door” Problem:
Passwords and Authentication Done Right
Passwords are not dead. They are just frequently mistreated.
NIST’s digital identity guidance (SP 800-63B-4) is clear about what helps and what does not. In particular, NIST states that verifiers should not impose arbitrary composition rules (like forced mixtures of character types) and should not require periodic password changes unless there is evidence of compromise. It also recommends screening proposed passwords against a blocklist of commonly used or compromised passwords, allowing password managers and autofill, and permitting paste when entering passwords (NIST, 2025).
Best Practices for Occupational Health Environments
1.) Require multi-factor authentication (MFA) everywhere it matters.
Prioritize MFA for:
- Admin accounts
- Remote access
- Email and identity provider logins
- Employer portals and provider portals
2.) Treat password policy as a security control, not an HR ritual.
Good password policy is designed to reduce account takeovers, not to create quarterly frustration. Adopt NIST-aligned practices: blocklist screening, no forced complexity rules, no forced periodic rotation without compromise evidence, and support password managers.
3.) Make phishing-resistant options the direction of travel.
If your identity provider supports phishing-resistant authentication methods, plan a phased rollout for privileged users first, then for all users who access sensitive records. NIST’s guidance discusses phishing resistance and encourages its use in higher assurance contexts.
Audit Logs: Your Best Friend After “What Just Happened?”
In occupational health, audit logs serve two purposes:
1.) Security: Detect suspicious access, investigate incidents, contain damage
2.) Trust and Accountability: Demonstrate who accessed what and when
If security tools are the locks, audit logs are the security camera footage. You hope you never need them, but you absolutely do not want to discover they were off after something goes wrong.
HIPAA Security Rule Expectations
(And Why They’re Useful Even Beyond HIPAA)
The HIPAA Security Rule includes:
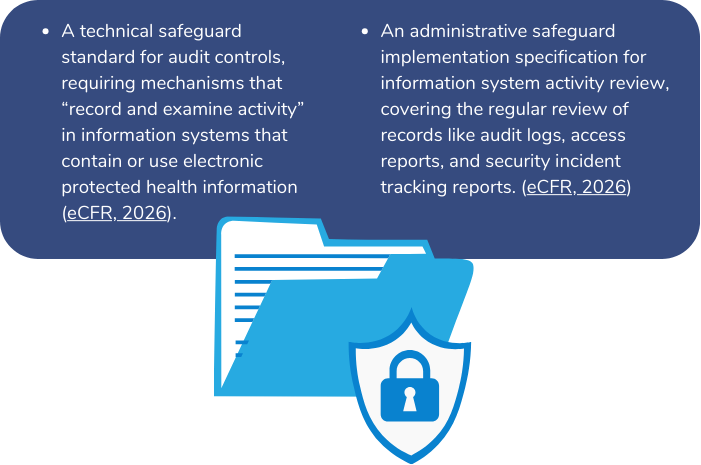
Practical Logging Guidance for Occupational Health Operations
Focus logs on events that matter:
- Authentication events: logins, failures, MFA resets, password resets
- Privileged actions: role changes, permission grants, admin configuration
- Record access: view, create, modify, export, print
- Integration activity: API calls, token creation, high volume requests, failed auth
- Data movement: bulk downloads, unusual exports, report generation spikes
Operationally:
- Centralize logs (avoid “it’s on that one server somewhere”)
- Protect logs from tampering (limited access, write once options where feasible)
- Set retention that supports investigations and contractual requirements
- Create alerts for patterns, not just single events (impossible travel, unusual exports, repeated failures)
Risk Analysis: The Foundation that Keeps Security Work from Turning into Whack-a-Mole
Security programs fail when they become a grab bag of tools instead of a managed risk program.
HHS OCR’s risk analysis guidance describes risk analysis as foundational for Security Rule compliance and emphasizes that it is an ongoing process, not a one-time exercise (HHS, n.d.).
For occupational health organizations, a risk analysis should explicitly include:
- Employer and provider portals (and role-based access design)
- Lab and EHR interfaces, including token and key management
- Remote work and contractor access
- Third-party vendors that store or process sensitive data
- Business continuity risks, especially around ransomware and downtime during hiring surges
Ransomware Readiness: Resilience Beats Heroics
Ransomware is not just encryption anymore. Extortion often includes data theft plus disruption pressure.
HHS OCR’s ransomware fact sheet explains that ransomware incidents can be security incidents and may trigger breach notification obligations depending on whether there is an impermissible disclosure of protected health information.
Core Controls that Reduce Ransomware Impact
- MFA and least privilege (reduces initial access and lateral movement)
- Patch and vulnerability management (removes easy exploit paths)
- Network segmentation (limits blast radius)
- Offline, immutable, and tested backups (restoration is a process, not a hope)
- Incident response playbooks and tabletop exercises (decisions are faster under stress when you have practiced)
If you only do one thing this quarter: verify that backups can actually restore the systems that run scheduling, results reporting, and client access. Backups that exist but cannot restore are just expensive comfort objects.
Vendor and Integration Risk: Your Ecosystem is Part of Your Attack Surface
Occupational health is highly interconnected: labs, provider networks, employers, background screening, HRIS, EHRs, and billing.
HICP technical guidance emphasizes managing vendor cybersecurity risk, including monitoring and documentation expectations, and highlights the importance of agreements and clear requirements around access and data handling.
Minimum Expectations to Set With Vendors
Include, at a minimum:
- Security requirements for authentication (MFA for administrative access)
- Breach notification timelines and cooperation obligations
- Subprocessor disclosure and controls
- Logging and audit support expectations
- Data return and destruction requirements at contract termination
- Evidence expectations (SOC 2 reports, third-party assessments, or equivalent)
Organizing Your Program with NIST CSF 2.0
NIST CSF 2.0 provides a clean structure: Govern, Identify, Protect, Detect, Respond, Recover, and it is designed for organizations of all sizes and sectors (NIST, 2024).
Here is an occupational health translation:
- Govern: define security ownership, policies, third party risk expectations, and reporting
- Identify: inventory systems, integrations, data types, and critical workflows
- Protect: MFA, access controls, encryption, secure configuration, training
- Detect: audit logs, monitoring, alerting, anomaly detection
- Respond: incident plan, roles, communications templates, vendor contacts
- Recover: backup restore testing, disaster recovery priorities, post incident improvements

Conclusion
Cybersecurity in occupational health is less about chasing the latest threat and more about executing the basics reliably: strong authentication, least privilege access, audit logging, and tested recovery. Using a risk framework like the NIST Cybersecurity Framework 2.0 helps teams translate those basics into repeatable outcomes across governance, protection, detection, response, and recovery (NIST, 2024). Just as important, HHS emphasizes that risk analysis should be an ongoing process so controls evolve as your systems, vendors, and workflows change (HHS, n.d.).
From a compliance and client trust standpoint, audit logs are a cornerstone. The HIPAA Security Rule calls for audit controls that record and examine activity in systems containing or using ePHI (Electronic Code of Federal Regulations, 2026). And because ransomware remains a leading operational threat in healthcare, incident readiness, MFA, and recoverability planning should be treated as business continuity controls, not just IT tasks (HHS, 2016).
BlueHive supports this direction by centralizing occupational health workflows and connecting organizations to a network of 22,000+ providers, reducing the need for ad hoc workarounds that can increase exposure. BlueHive AI also aims to streamline work processes and improve productivity, which helps security stick because secure workflows are easier to follow when they are also easier to use.
Sources
- Electronic Code of Federal Regulations. (2026). 45 CFR § 164.308 Administrative safeguards. Retrieved January 9, 2026, from https://www.ecfr.gov/current/title-45/subtitle-A/subchapter-C/part-164/subpart-C/section-164.308
- Electronic Code of Federal Regulations. (2026). 45 CFR § 164.312 Technical safeguards. Retrieved January 9, 2026, from https://www.ecfr.gov/current/title-45/subtitle-A/subchapter-C/part-164/subpart-C/section-164.312
- National Institute of Standards and Technology. (2024). The NIST Cybersecurity Framework (CSF) 2.0 (NIST CSWP 29). https://doi.org/10.6028/NIST.CSWP.29 (PDF available at https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.29.pdf)
- National Institute of Standards and Technology. (2025). Digital identity guidelines: Authentication and authenticator management (NIST SP 800-63B-4). https://doi.org/10.6028/NIST.SP.800-63B-4 (PDF available at https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-63b-4.pdf)
- U.S. Department of Health and Human Services, Office for Civil Rights. (2016, July 11). Fact sheet: Ransomware and HIPAA. https://www.hhs.gov/sites/default/files/RansomwareFactSheet.pdf
- U.S. Department of Health and Human Services, Office for Civil Rights. (2024, December 27). HIPAA Security Rule NPRM. https://www.hhs.gov/hipaa/for-professionals/security/hipaa-security-rule-nprm/index.html
- U.S. Department of Health and Human Services. (n.d.). Guidance on risk analysis. Retrieved January 9, 2026, from https://www.hhs.gov/hipaa/for-professionals/security/guidance/guidance-risk-analysis/index.html
- Verizon. (2024). 2024 Data Breach Investigations Report. https://www.verizon.com/business/resources/T387/reports/2024-dbir-data-breach-investigations-report.pdf
- 405(d) Health Industry Cybersecurity Practices (HICP). (2023). Technical Volume 1: Cybersecurity practices for small healthcare organizations. https://healthsectorcouncil.org/wp-content/uploads/2023/01/tech-vol1-508.pdf




